Securinets Friendly CTF 2k22
My web Tasks for Securinets Friendly CTF 2k22
Intro
Securinets Friendly CTF is our very first CTF for 2022-2O23 academic year. It’s meant to be for early beginners without prior knowledge in order to introduce them to the field. This CTF was 5 days long and was launched after 4 hours Introduction To Cybersecurity training.
I’am really blessed with the huge amount of satisfaction and feedbacks that we received from the players.
Kudos to all the authors for the 113 creative and well structured challenges.
Stats

Web Writeups
I’am writing this for the people who asked about solutions, hope you find this helpful.
| Task Name | Solves |
|---|---|
| Welcome | 155 |
| Web Crawler | 153 |
| JW token | 145 |
| Request basics 1 | 135 |
| LoGic? | 113 |
| NFT Marketplace | 107 |
| Request basics 2 | 106 |
| Request basics 3 | 92 |
| COOOOOOOOkiiie | 86 |
| XXdirect | 74 |
| Halt and Catch Fire | 43 |
| Tunisia | 29 |
Eventhough the tasks are basic, all my web challs were well guided with source code available.
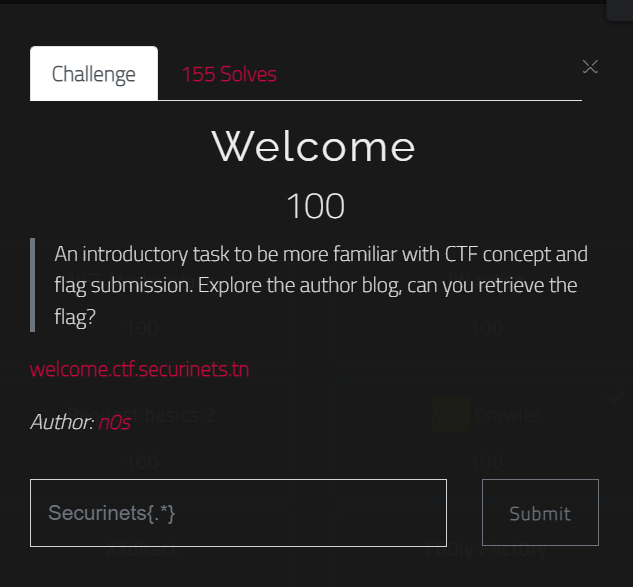
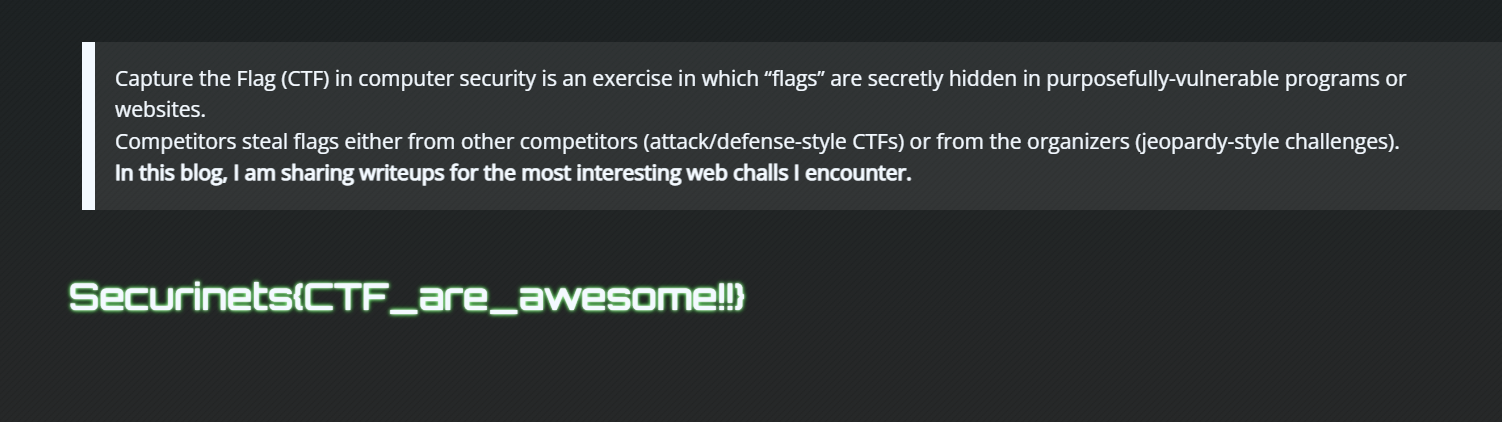
Welcome
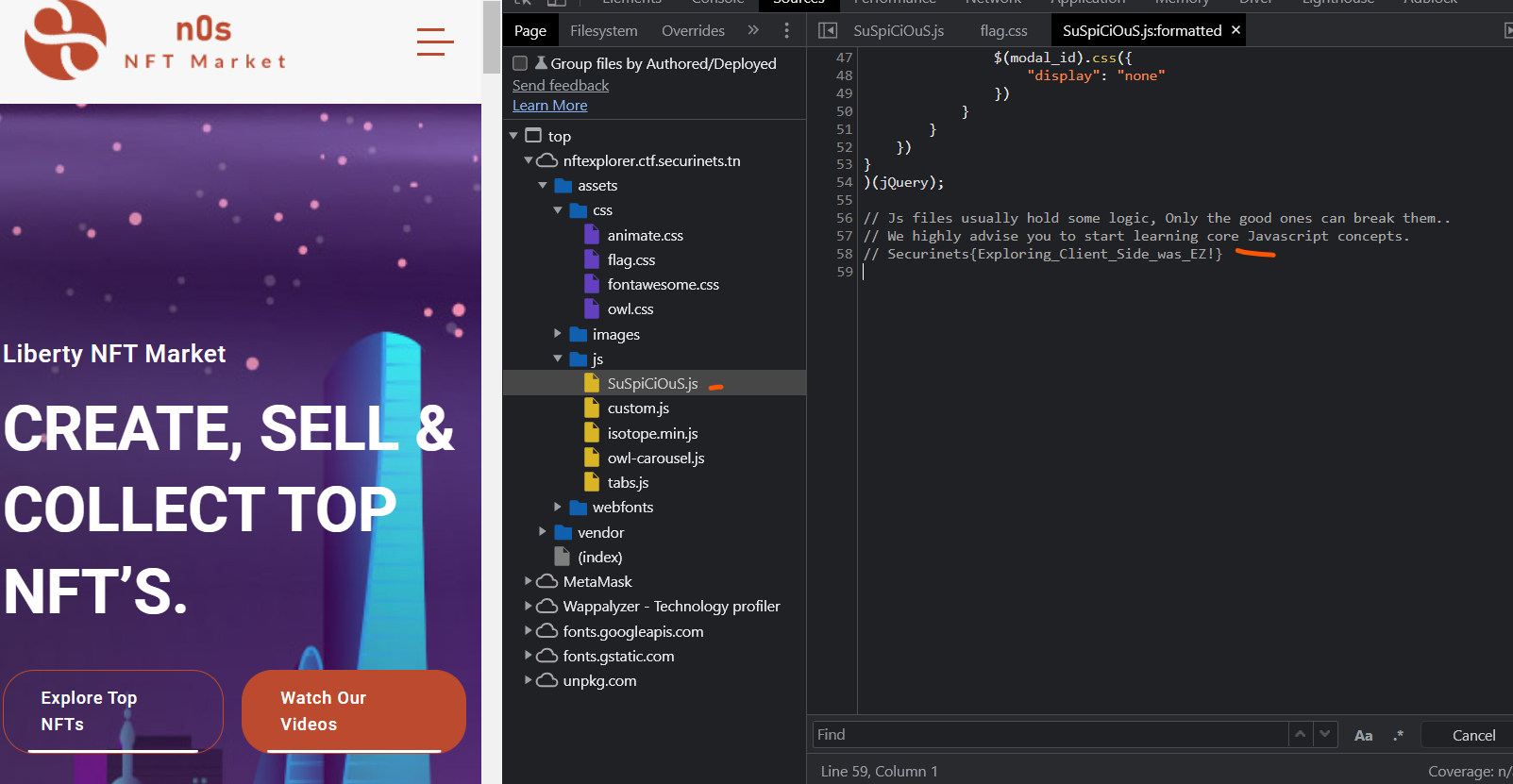
NFT Marketplace


JW token

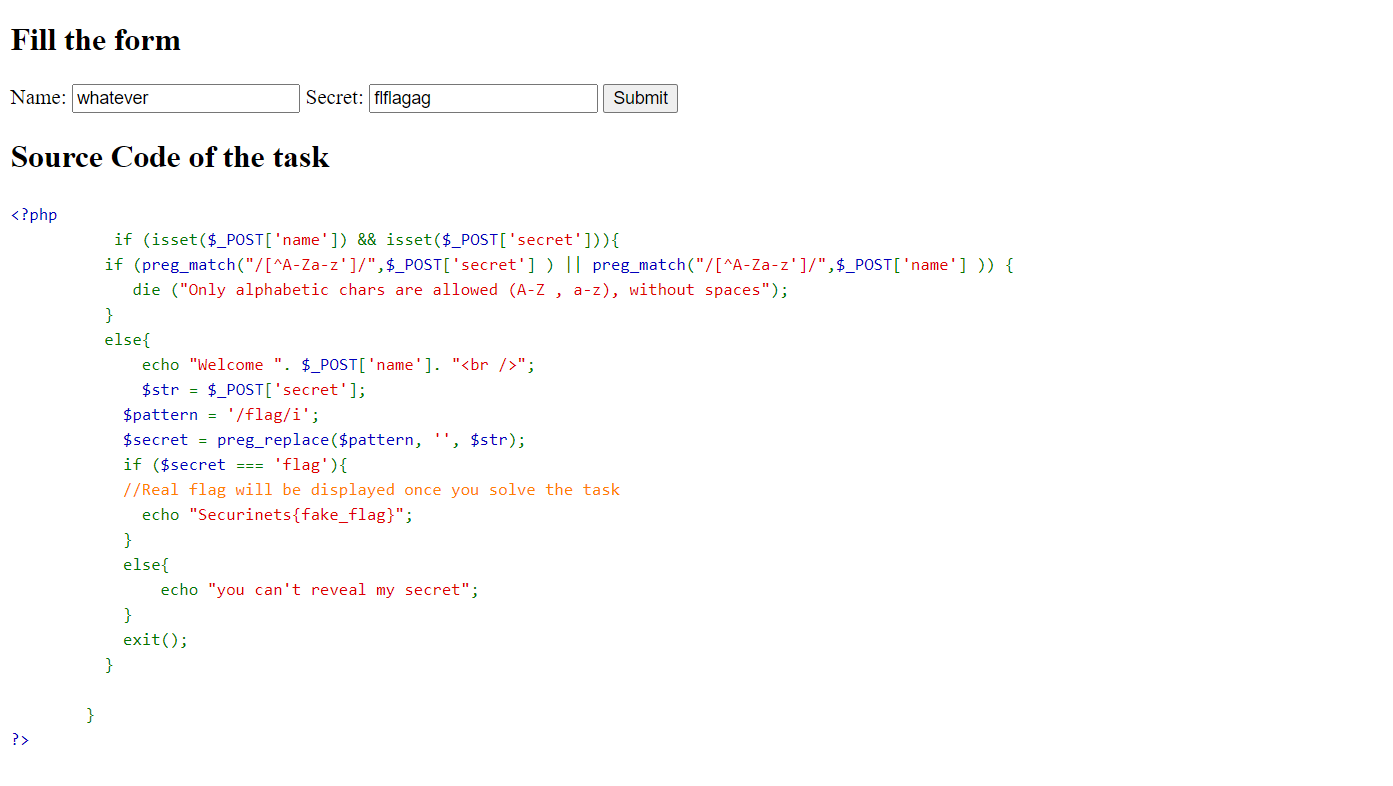
LoGic?

preg_replace() in php replaces only once.

Request basics 1



Request basics 2


Request basics 3

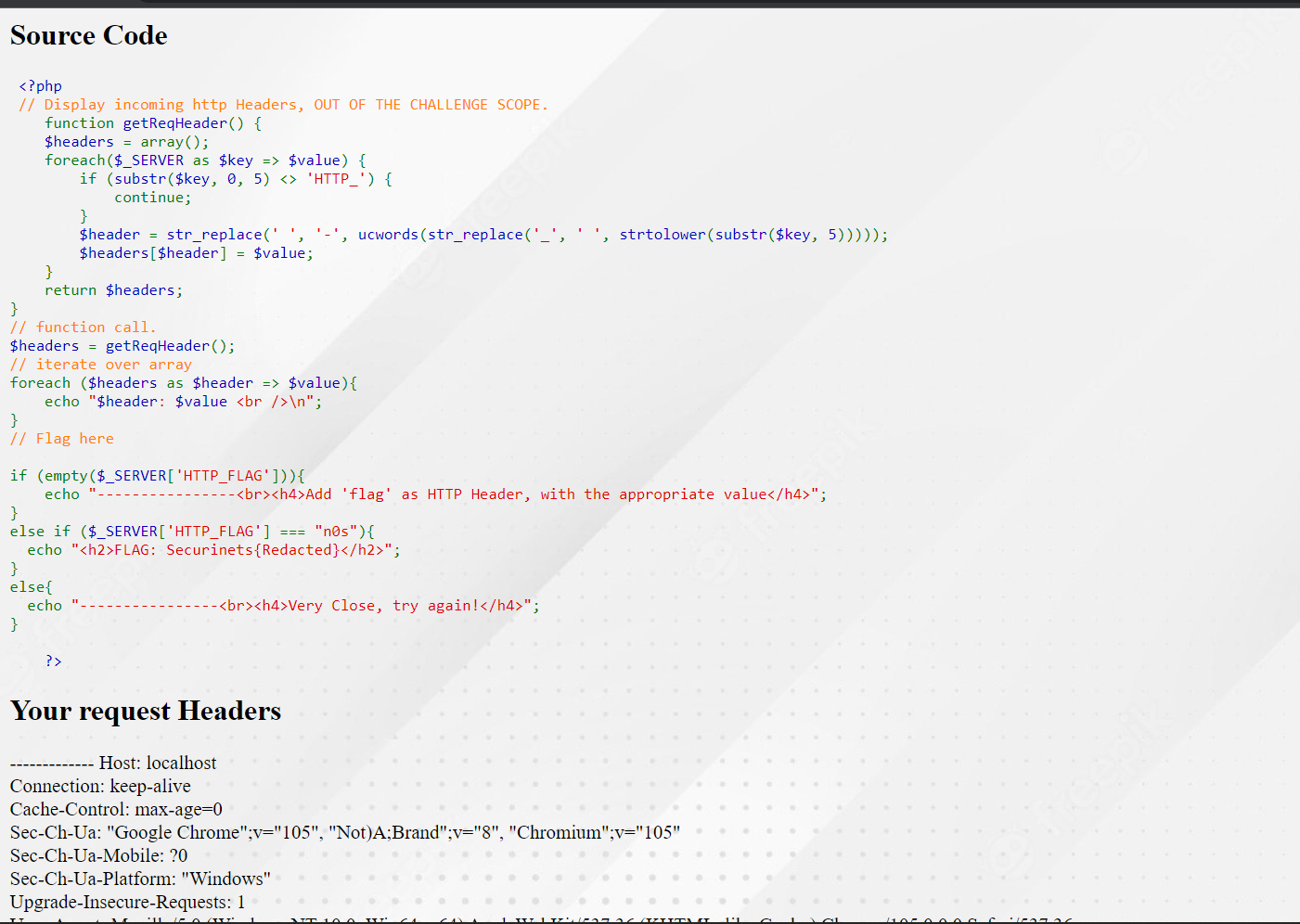

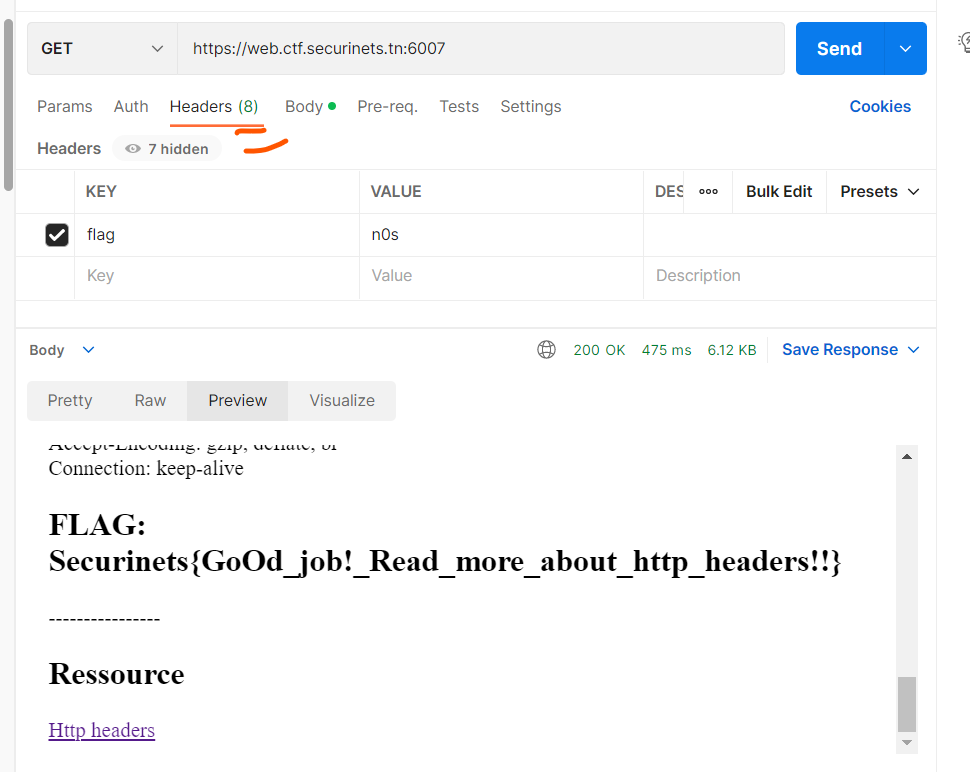
Web Crawler


COOOOOOOOkiiie

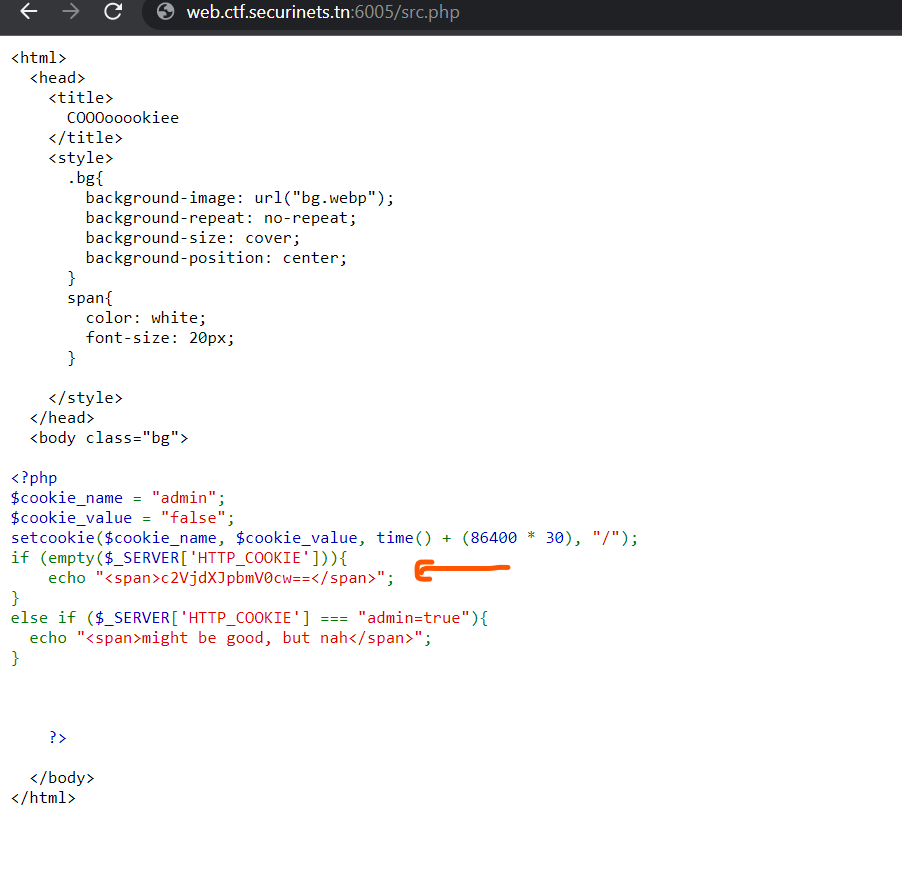
all you have to do is to delete the Cookie
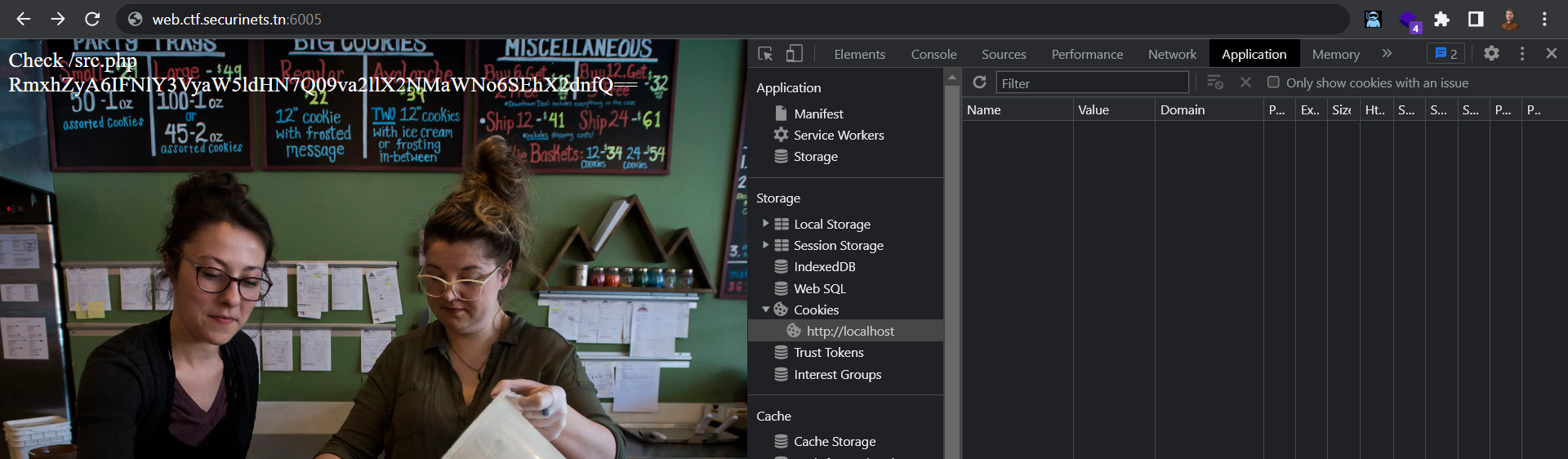
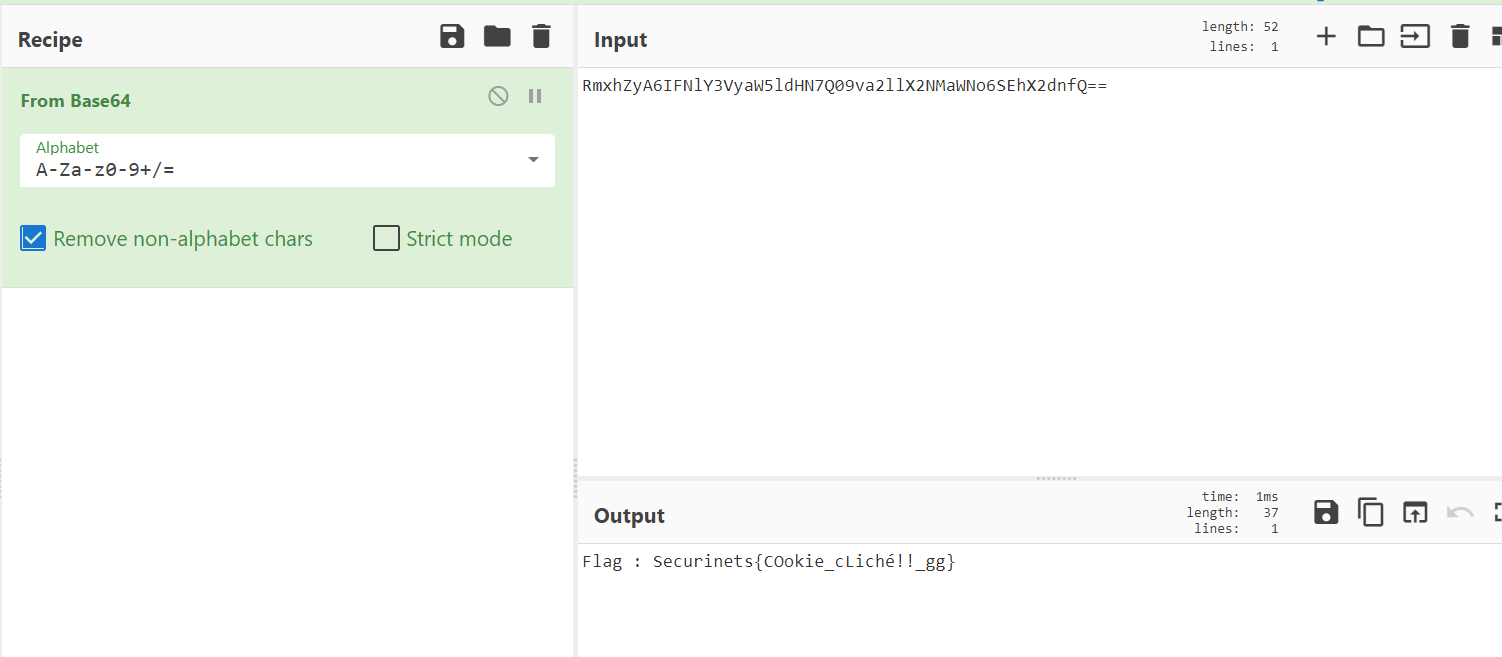
Then, decode with cyberchef (online website)
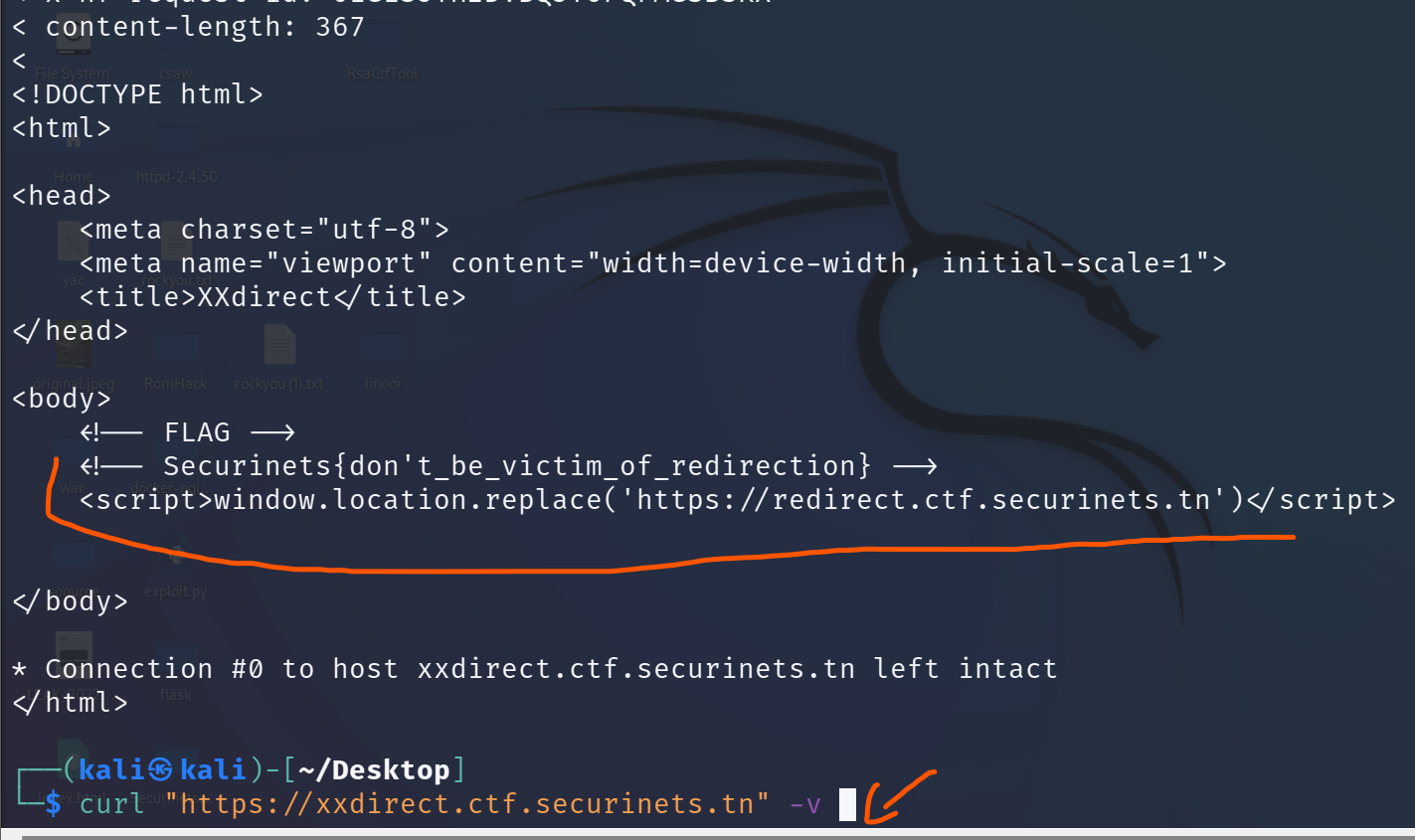
XXdirect

You should notice that the Url changes from XXdirect.ctf.securinets.tn to redirect.ctf.securinets.tn

all you have to do is to see raw response from the first url
Halt and Catch Fire

Some players were trying to deobfuscate JS and ended up with a
single part of the flag, that’s nice but the intended solution
is to expose players to Browser debug mode.

Tunisia
The least solved one,

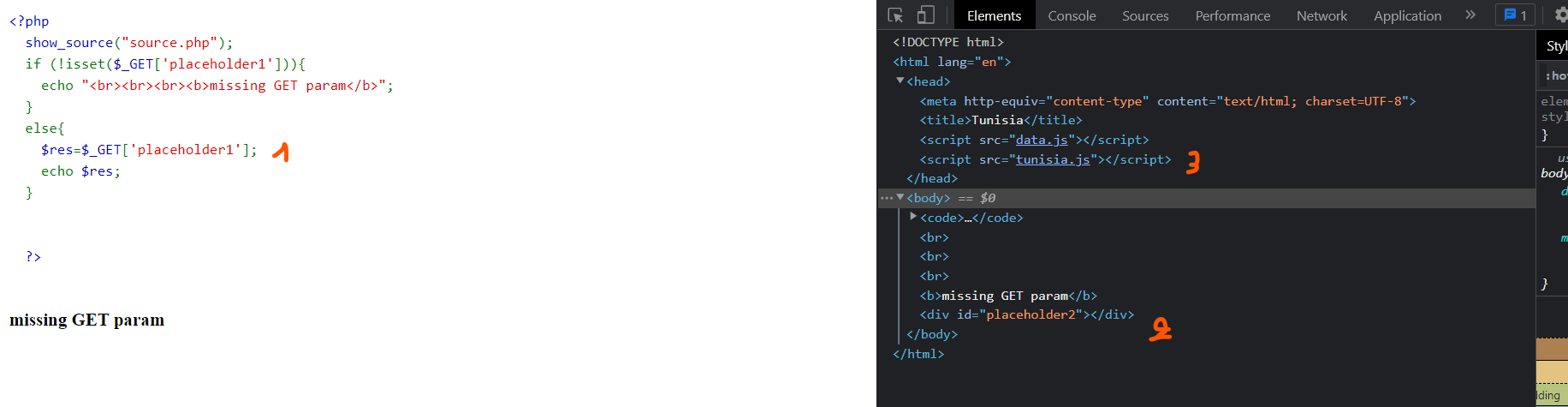
You should notice that whatever input in placeholder1 param gets injected in html code.
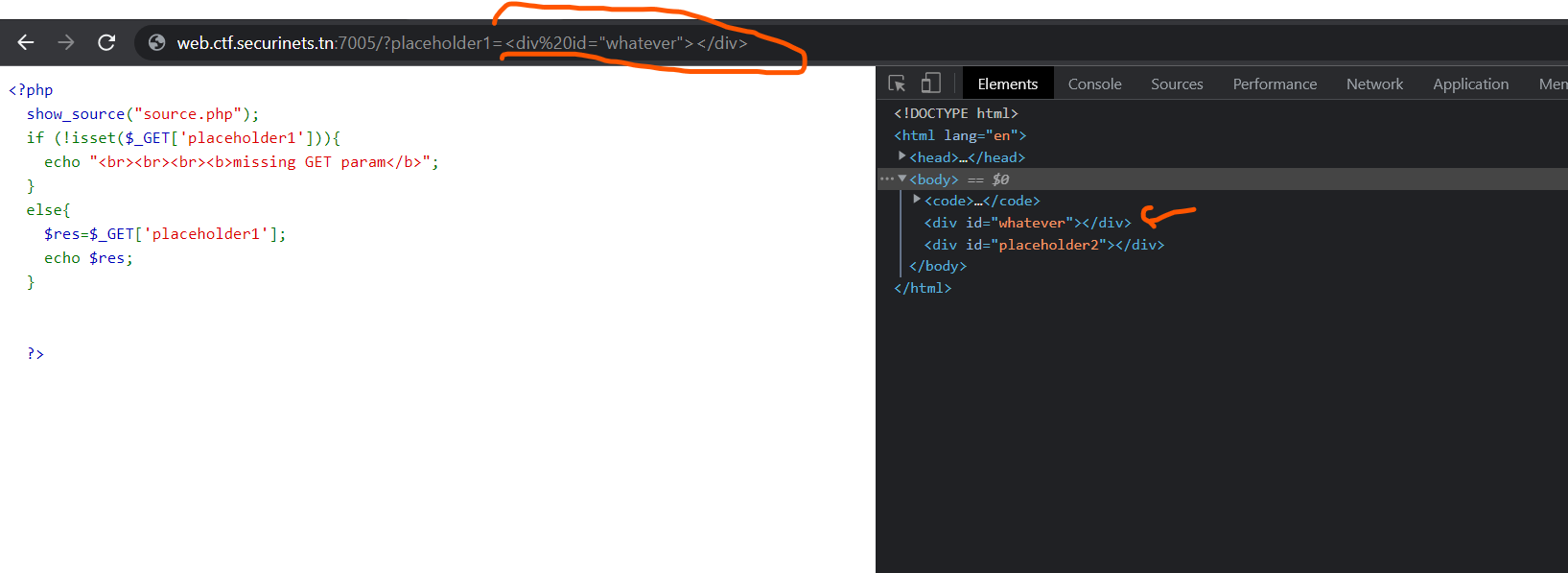
I already gave you the format of the injection with the attribute id=”placeholder2” to modify : all you have to do is to google how js is interacting with html and thus you’ll find the known js method : getElementById

Searching in Tunisia.js, you’ll find that if the div element isn’t “map”, there will be a console logging of the char “-“
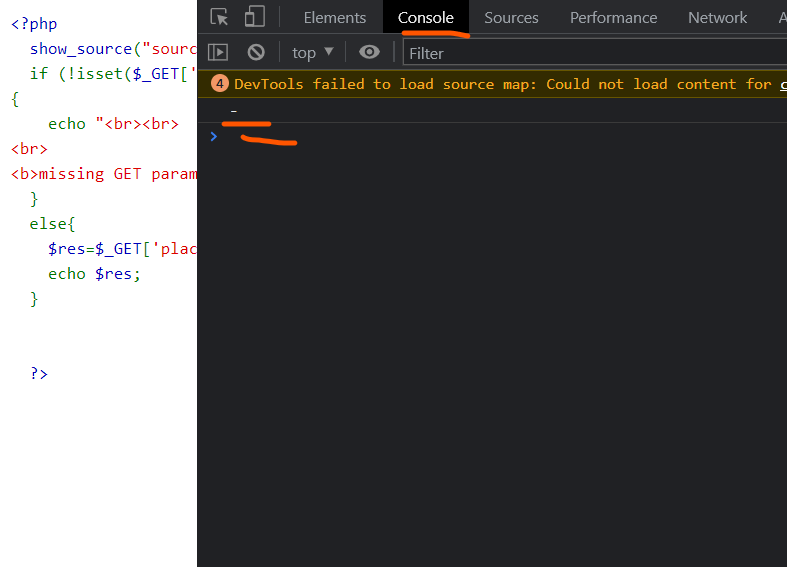
solution : web.ctf.securinets.tn:7005/?placeholder1=<div id=”map”></div>
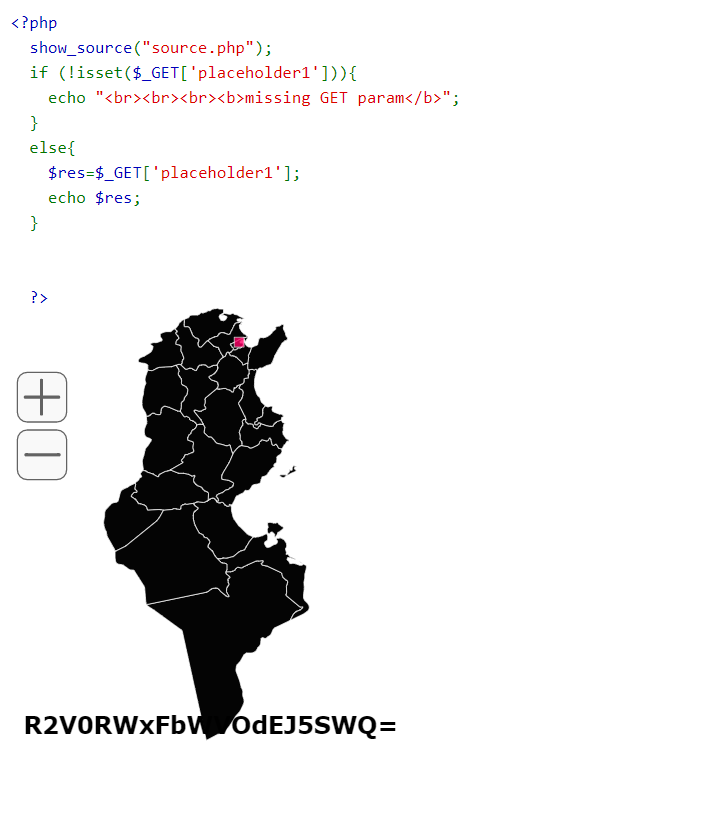
with base 64 decoding the secret is : GetElEmeNtById
flag : Securinets{GetElEmeNtById}
Conclusion
To all players who joined us, no matter what you solved, we are proud of you and we hope to see you soon in our upcoming workshops.
To all Tunisian Cybersecurity enthusiasts, reach us if you feel that we can help you, it’s our pleasure, we’re learning new stuffs everyday and we don’t mind sharing them with you.